Block users from logging in on Windows devices (via Intune)

Introduction
In the effort of terminating individual users you may be required to block them from being able to access their Windows devices (logging in). This may be to prevent them from exfiltrating data (downloading stuff, copying work over on USB sticks etc.), or to limit their capability of doing harm to the organization, especially in the event that their leave is unconsensual. This blog post can help you achieve this task. Assumption here is that you are managing devices via Intune (devices are Enrolled).
Configuration
We'll split this into 2 parts:
1. Blocking the Guests (local) group from logging in
2. Adding your target 🎯 group as a member of the Guests (local) group
1. Blocking the Guests (local) group from logging in
OK, going back to Windows98, the Local Users and Groups console was introduced. You can access it by pressing Start menu / Windows key and typing "lusrmgr.msc".

The console is basically unchanged for the past 20 years. In it you'll find the "Guests" group which contains the "Guest" user, which by default is disabled.
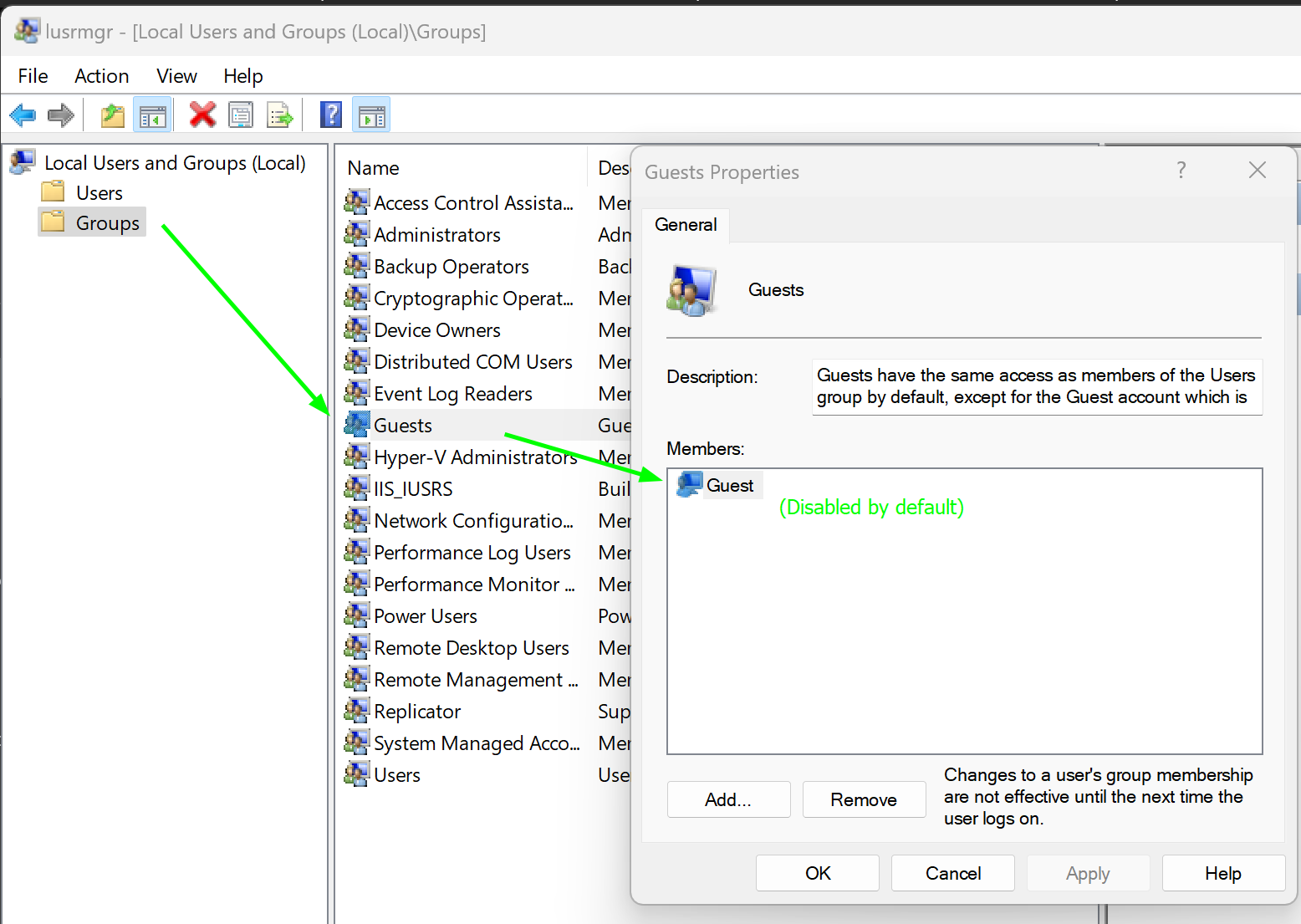
All these built-in groups are documented on MS articles and their SIDs (security identifiers) are public information. Thus we can block the Guests group altogether as this has a very low risk of causing collateral damage.
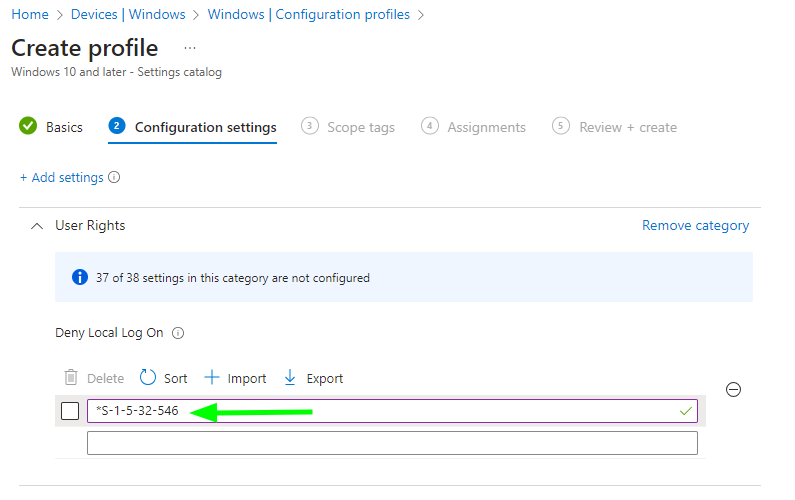
In order to block the Guests group, we create this Settings catalog in Intune,
of type "User Rights",
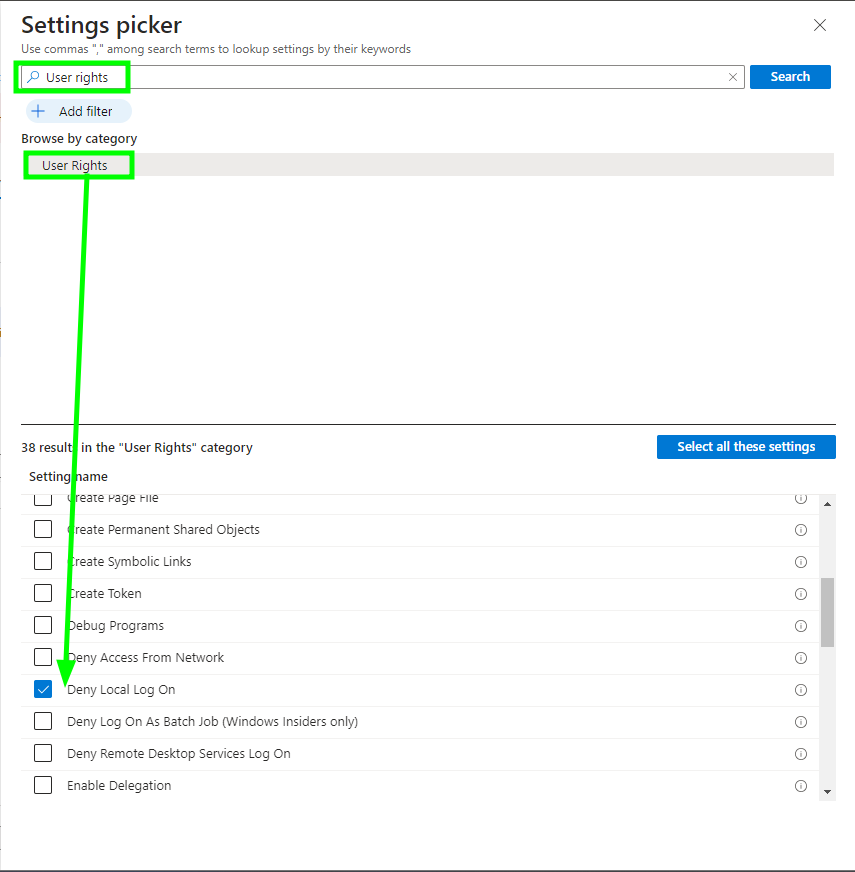
in which we configure the setting "Deny Local Log On" and we input the SID of the Guests group: *S-1-5-32-546
Full list of Well-Known SIDs in the documentation here.
We can apply this policy to All devices (after thoroughly testing via a pilot).
Result:
Guests (local) group will be blocked from logging into Windows.
See where I'm going with this? You just need to find a way to add your terminated user to be a member of the Guests group on his device. (Explained in the next section)
2. Adding your target 🎯 group as a member of the Guests (local) group
We will be adding our target user via a group. For the sake of this example I'll call mine TerminatedUsers:
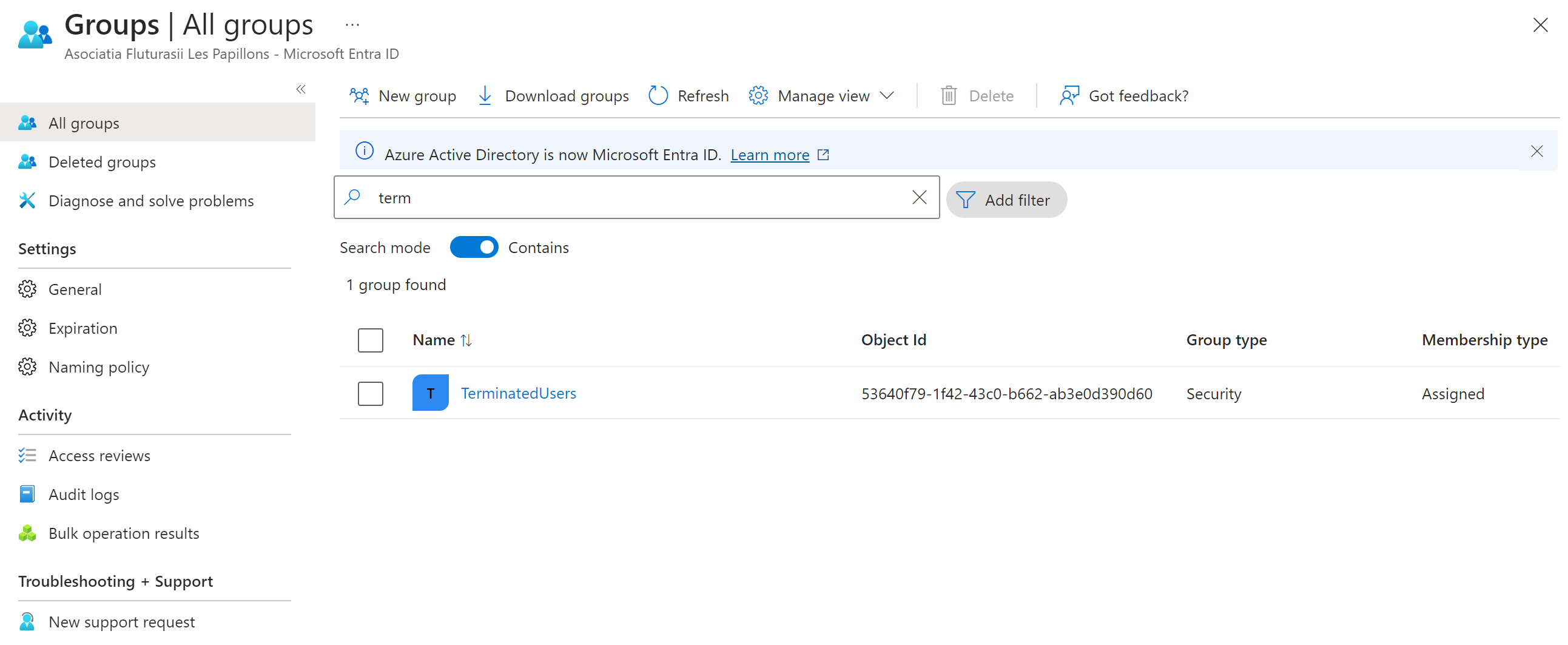
So whenever a user leaves/is laid off, I'll add that user to this group. Now how do we add this group to the Guests local group? Again with the help of Intune.
We create a Custom Profile (OMA Uri) this time around:
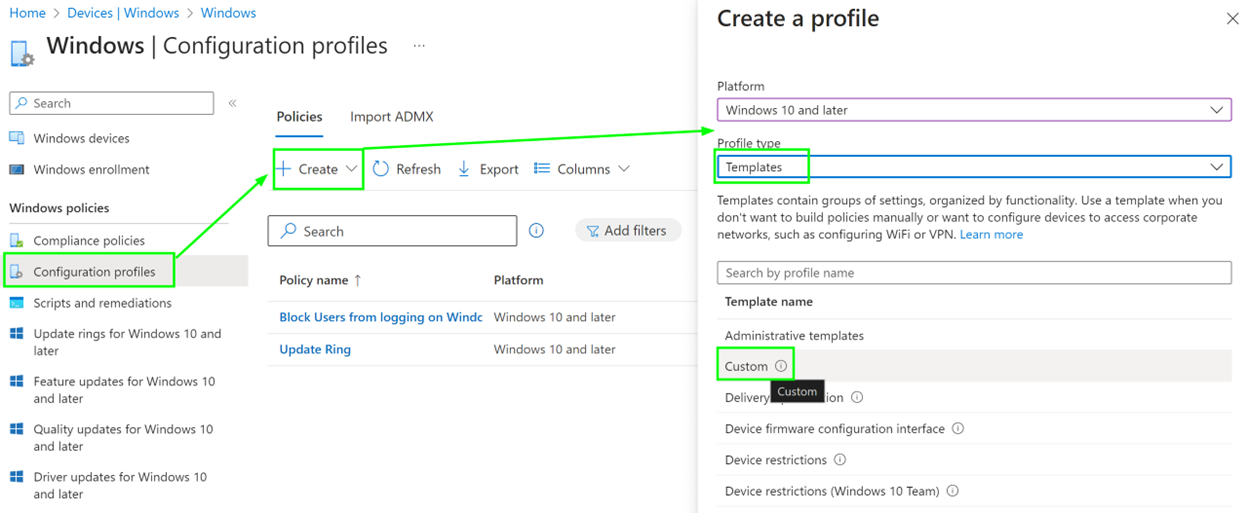
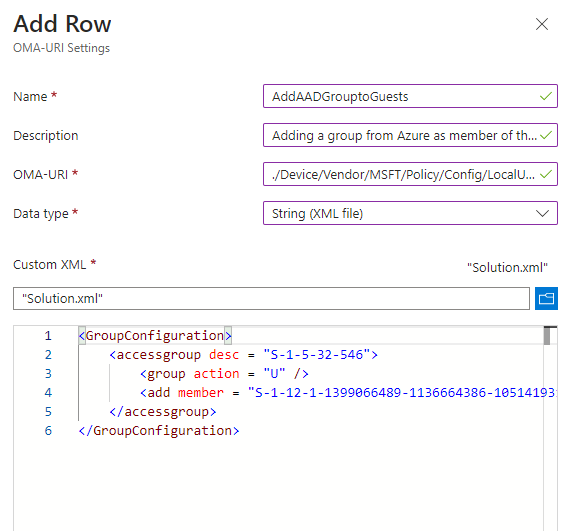
Add the OMA uri: ./Device/Vendor/MSFT/Policy/Config/LocalUsersAndGroups/Configure (more info on it, here)
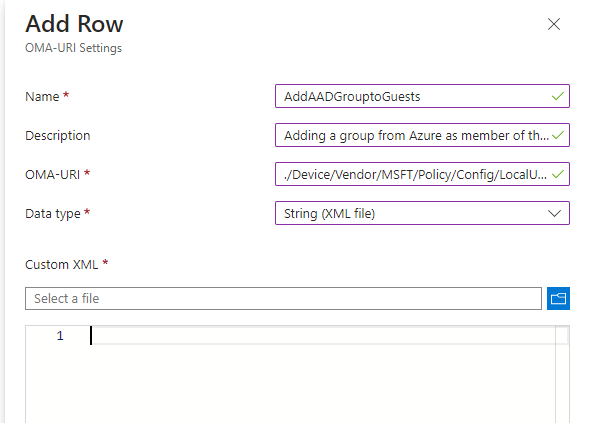
For the XML to use, simply open up a notepad, here's the sample, replace the SIDs with your own and save it as .xml then upload it:
<accessgroup desc = "S-1-5-32-546">
<group action = "U" />
<add member = "INSERT YOUR GROUP SID HERE"/>
</accessgroup>
Now, in order to find out the local SID of your own Offboarding group, you can go on https://aka.ms/ge which is Graph Explorer and you will have to input the following info:
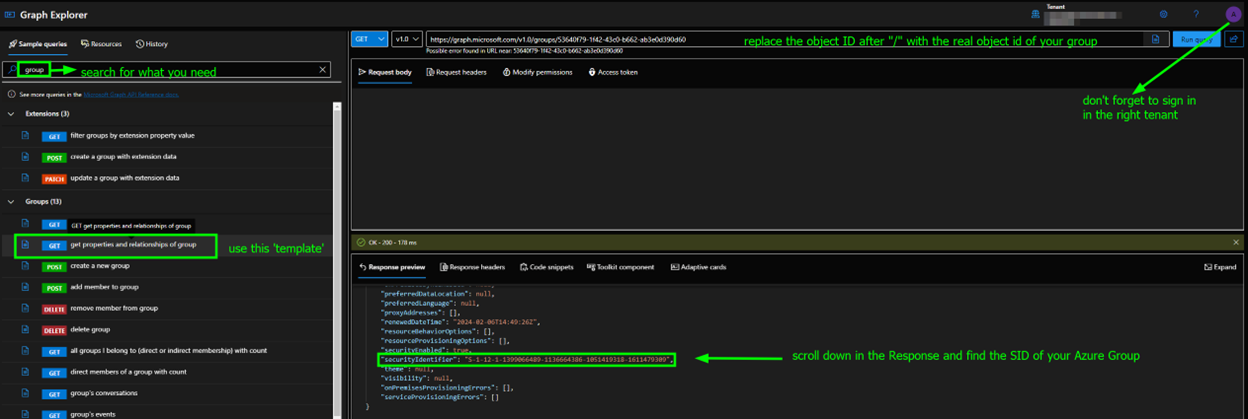
Use the obtained SID in your XML and upload it to the Custom Configuration Profile:
You can assign the Setting Catalog policy to All Devices (after thorough testing).
Result:
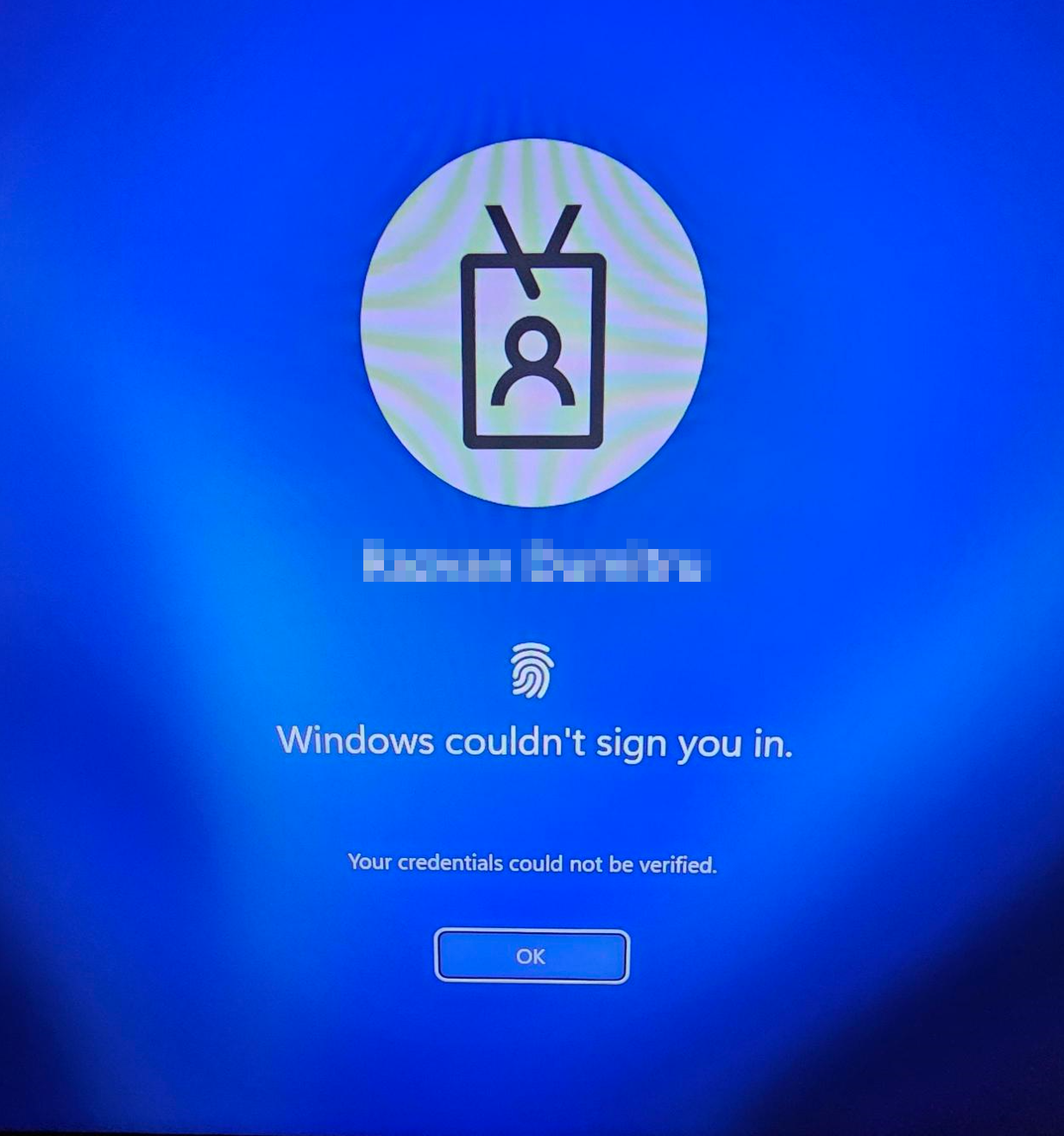
Whenever you add an user to the TerminatedUsers group, it will take a few hours for the group membership to be synced with the user's PC(s), but after it syncs, he'll be signed out and when he tries to sign in (including Windows Hello methods), he'll see this:
Conclusion
This solution helps you block users from logging on their Windows devices, and is composed of 2 policies in Intune that should:
- Block the local log on of the local Guests group
- Add to the local Guests group the members of the Azure group you are using for offboarding users in your org.
This can prevent misuse of devices by users that should no longer be able to log in.
